Sitemize üye olarak beğendiğiniz içerikleri favorilerinize ekleyebilir, kendi ürettiğiniz ya da internet üzerinde beğendiğiniz içerikleri sitemizin ziyaretçilerine içerik gönder seçeneği ile sunabilirsiniz.
EPOSTA ADRESİNİZ
Zaten bir üyeliğiniz mevcut mu ? Giriş yapın
Lütfen geçerli bir mail adresi giriniz.
Lütfen üyelik ve gizlilik sözleşmesini onaylayın.
Sitemize üye olarak beğendiğiniz içerikleri favorilerinize ekleyebilir, kendi ürettiğiniz ya da internet üzerinde beğendiğiniz içerikleri sitemizin ziyaretçilerine içerik gönder seçeneği ile sunabilirsiniz.
Üyelerimize Özel Tüm Opsiyonlardan Kayıt Olarak Faydalanabilirsiniz
Sıradaki içerik:
KVKK 16/05/2019 Tarihli ve 2019/138 Sayılı Karar Özeti
- Anasayfa
- Sanallaştırma
- VMware
- VMware Releases Fix for Critical vCenter Server Vulnerability
VMware Releases Fix for Critical vCenter Server Vulnerability
40 okunma
—
17 Nisan 2020 10:32

VMware released a security update that fixes a critical vulnerability in the vCenter Server virtual infrastructure management platform that could allow attackers to gain access to sensitive information and potentially take control of affected virtual appliances or Windows systems.
vCenter Server provides IT admins with centralized management of virtualized hosts and virtual machines within enterprise environments from a single console.
“With vCenter Server, virtual environments are easier to manage: a single administrator can manage hundreds of workloads, more than doubling typical productivity when managing physical infrastructure,” says VMware.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued an alert saying that an “attacker could exploit this vulnerability to take control of an affected system,” and encouraging users and administrators to update.
Critical flaw scoring a perfect 10 CVSSv3 score
Remediation measures
Remediation measures
The privately reported vulnerability is tracked as
CVE-2020-3952 and it was rated with a maximum CVSSv3 base score of 10 according to VMware’s security advisory.
This security issue affects the VMware Directory Service (vmdir) only on upgraded installations and it’s due to incorrectly implemented access controls.
vCenter Server 6.7 (embedded or external PSC) prior to 6.7u3f is affected by CVE-2020-3952 if it was upgraded from a previous release line such as 6.0 or 6.5. Clean installations of vCenter Server 6.7 (embedded or external PSC) are not affected. – VMware
“Under certain conditions vmdir that ships with VMware vCenter Server, as part of an embedded or external Platform Services Controller (PSC), does not correctly implement access controls,” VMware explains.
“A malicious actor with network access to an affected vmdir deployment may be able to extract highly sensitive information which could be used to compromise vCenter Server or other services which are dependent upon vmdir for authentication.”
Detailed steps on how to determine if your vCenter Server deployment is impacted by CVE-2020-3952 can be found in VMware’s KB78543 support document.
Due to the critical nature of this security vulnerability, it is strongly recommended that you upgrade vCenter Server as soon as possible.
To patch the vulnerability on your Windows or virtual appliance deployments you have to upgrade affected installations to deployment to vCenter Server 6.7u3f.
Last month VMware issued another security update to fix a Critical vulnerability in VMware Workstation Pro that could enable attackers to perform denial-of-service attacks or execute commands on the Windows host.
Four days later, VMware patched high severity privilege escalation and denial-of-service (DoS) flaws in the VMware Workstation, Fusion, VMware Remote Console and Horizon Client.
Benzer İçerikler
- Site İçi Yorumlar
Hızlı Yorum Yap

TREND İÇERİKLER
Yedeklemede 3-2-1 Kuralı Nedir?
0
Ağustos 26, 2024
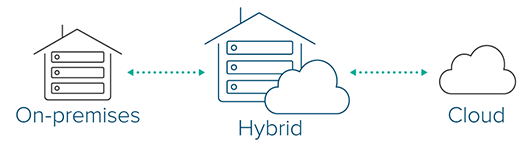
Comprehensive Comparison: Cloud vs On-Premises vs Hybrid-Cloud Solutions
0
Haziran 21, 2024
Citrix Systems kimdir?
0
Aralık 6, 2022




















Yorum Yaz